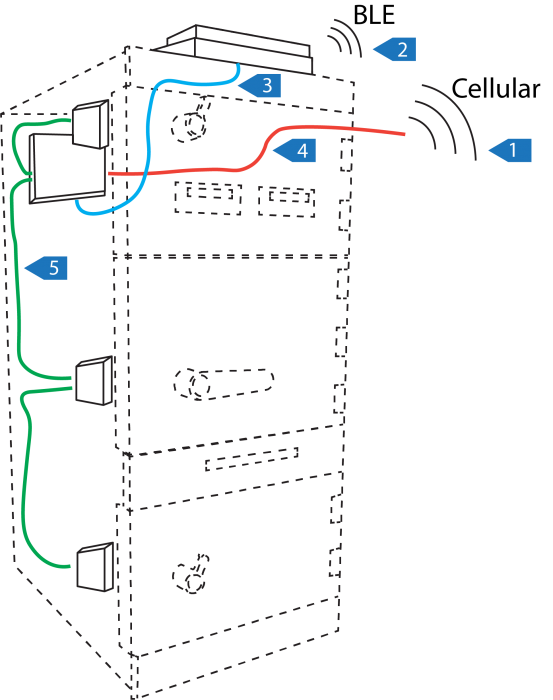
Encryption of Data Inside and Out
In a smart safe, money is converted into data. That data flows from the safe controller out to web services where it often results in provisional credit in a customer’s bank account.
Data is converted back into money when a cash collection occurs and a user presents data in the form of a credential to open the safe and access the cash.
Whether the data path leaves the safe or remains internal to the safe, the data needs to be protected to avoid manipulation and exploitation.
In the diagram below, click the numbered labels to explore the ways we encrypt our data.
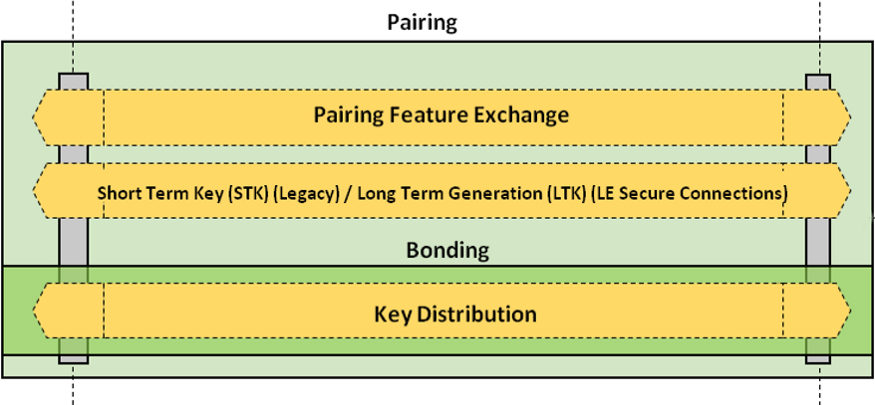
Encryption Technologies
4G Encryption
4G LTE encryption provides robust protection of data from the safe's embedded modem to the internet base station.
BLE Secure Pairing
Bluetooth Low Energy v5.0 offers secure over-the-air communications between our equipment and smart devices that are highly resilient to hacking and man-in-the-middle attacks.
User Interface Link
We encrypt all our sensitive authentication and reporting data that flows between the safe controller and the user interface.
Vcomm Encryption
Remote management of the safe is possible with our Vcomm protocol library. All sensitive data over this exchange is end-to-end encrypted.
6DBT Comm Link
Communications to our patented 6DBT door locks are fully encrypted to protect against direct attempts to hack our locks.
4G Cellular communications are highly secure and ubiquitous. We routinely rely on this infrastructure for the privacy of our voice calls, internet browsing, and data exchanges.
All communications that occur through cellular are encrypted. The encryption used in 4G networks is enhanced over previous cellular network generations. It provides a robust, secure link of data from equipment out to the base station unlike hardwire Ethernet or in-store Wi-Fi networks whose security is subject to local configuration.
By using 4G Cellular, complexities of dealing with store IT equipment and policies is avoided and a secure convenient plug-and-play safe installation is possible.
Further Reading:
NIST Study of LTE Security
Bluetooth Low Energy (BLE5) is presently available in just about every make and model of smart phone, tablet, and laptop computer. It enables rich interactions between smart device applications and hardware accessories.
Part of the BLE5 specification is a highly secure pairing and data encryption scheme designed to prevent sniffing and hacking of data exchanges over-the-air.
We use BLE to extend our equipment’s user interface to smart devices with our CTConnect protocol which is itself encrypted at the application layer so that it is protected both over-the-air and on the wire at both ends.
Further Reading
Data exchanged between the safe controller and our user interface contains sensitive data such as log in credentials, settings configurations, and summary financial data. Strong application level encryption is used to prevent hacking.

Our VComm protocol is a comprehensive library of data exchange functions used for the exchange of safe activities, configuration data, and firmware updates with web services.
Data in this protocol is encrypted at the application layer using a shared key with the web services. This offers robust data privacy and resilience to hacking even when using a public network connection.

Our 6DBT locking system is responsible for opening doors in coordination by the command of our safe controller.
The communication interface to these locks are encrypted with a rolling scheme that prevents the use of replay attacks.